Since 2019, we’ve been committed to providing the best value in the I.T Support business. Now, no matter what your server needs are, you can trust Beuker I.T Services to deliver a world-class experience. Enjoy the benefits of 2hr average provisioning time, 100% Uptime SLA, Free Setup Assist Service, 24/7/365 Customer Support, 24/7 Hardware Replacement, Full Root Access on all dedicated servers, No Contract – Month-to-Month billing, 7-day Money Back Guarantee, 100Mbps, 1Gbps, or 10Gbps Uplink Ports, Premium Multi-Homed Bandwidth, and more!
Private VPN
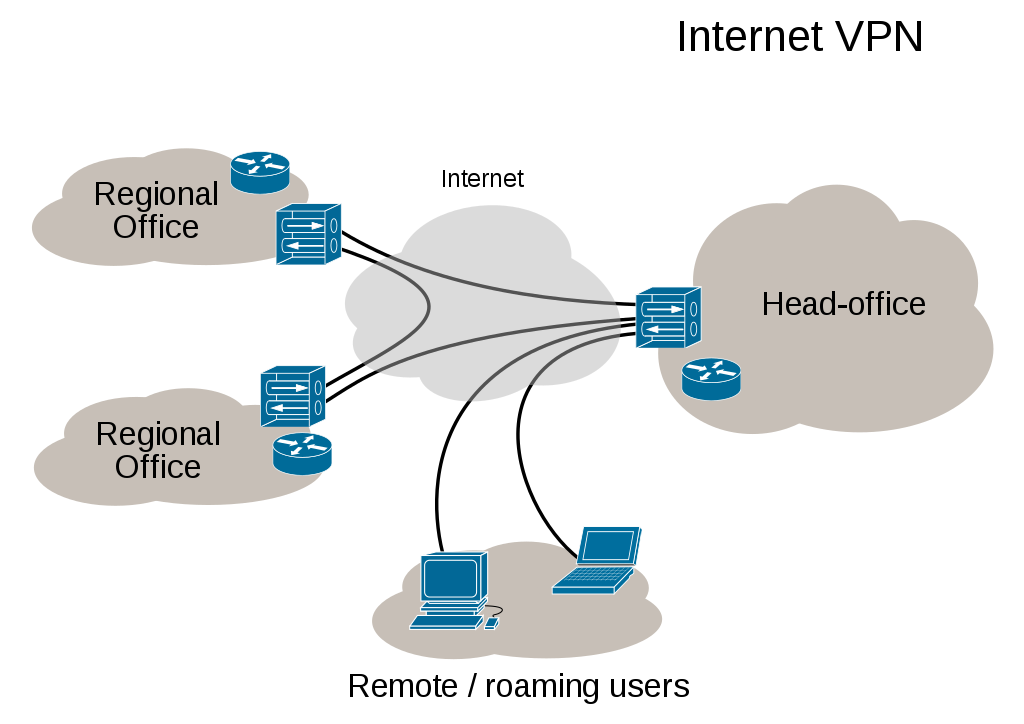
A virtual private network (VPN) extends a private network across a public network, and enables users to send and receive data across shared or public networks as if their computing devices were directly connected to the private network. Applications running on a computing device, e.g. a laptop, desktop, smartphone, across a VPN may therefore benefit from the functionality, security, and management of the private network. Encryption is a common though not an inherent part of a VPN connection.[1]
VPN technology was developed to allow remote users and branch offices to access corporate applications and resources. To ensure security, the private network connection is established using an encrypted layered tunneling protocol and VPN users use authentication methods, including passwords or certificates, to gain access to the VPN. In other applications, Internet users may secure their transactions with a VPN, to circumvent geo-restrictions and censorship, or to connect to proxy servers to protect personal identity and location to stay anonymous on the Internet. However, some websites block access to known VPN technology to prevent the circumvention of their geo-restrictions, and many VPN providers have been developing strategies to get around these roadblocks.
A VPN is created by establishing a virtual point-to-point connection through the use of dedicated circuits or with tunneling protocols over existing networks. A VPN available from the public Internet can provide some of the benefits of a wide area network (WAN). From a user perspective, the resources available within the private network can be accessed remotely.
Dedicated Server Support
Managed hosting service is a type of Internet hosting in which the client leases an entire server not shared with anyone else. This is more flexible than shared hosting, as organizations have full control over the server(s), including choice of operating system, hardware, etc. There is also another level of dedicated or managed hosting commonly referred to as complex managed hosting. Complex Managed Hosting applies to both physical dedicated servers, Hybrid server and virtual servers, with many companies choosing a hybrid (combination of physical and virtual) hosting solution. There are many similarities between standard and complex managed hosting but the key difference is the level of administrative and engineering support that the customer pays for – owing to both the increased size and complexity of the infrastructure deployment. The provider steps in to take over most of the management, including security, memory, storage and IT support. The service is primarily proactive in nature.[1] Server administration can usually be provided by the hosting company as an add-on service. In some cases a dedicated server can offer less overhead and a larger return on investment. Dedicated servers are hosted in data centers, often providing redundant power sources and HVAC systems. In contrast to colocation, the server hardware is owned by the provider and in some cases they will provide support for operating systems or applications.[citation needed]
Using a dedicated hosting service offers the benefits of high performance, security, email stability, and control. Due to the relatively high price of dedicated hosting, it is mostly used by websites that receive a large volume of traffic.
Remote Support
In information technology (IT), remote support tools are IT tools and software that enable an IT technician or a support representative to connect to a remote computer from their consoles via the Internet and work directly on the remote system[1]. Although its main focus is the access to computers located anywhere in the world, the remote support applications also provide features like file transfer, desktop sharing, file synchronization, command line or guest accessibility.
Privacy
Privacy is also a major concern for all users. One of the most used tools in remote support sessions are the ones that allow desktop sharing. It is also possible to provide what is commonly called Unattended Support (the technician is granted total remote access to the client’s computer, even when he is not physically close to it). The need for an absolute trust in these services and providers is considered to be the biggest obstacle for this technology to achieve mass-marketing status – even when many studies indicate that for every 5 technical occurrences, 4 of them could be remotely solved.
Benefits
Remote Support technology tries to reduce helpdesk centers cost-issues – all transport-related expenses are immediately trimmed down, for instance. Modern day technology enables that any technician using Remote Support is able to assist a customer just like it was physically side-by-side. Technologies and tools like live chat, VoIP and desktop sharingenable a direct intervention in the remote system.

